Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

Earlier this month, we wrote about Insider Threat Awareness Month. The program is led by the National Insider Threat Task Force (NITTF), and others to help organizations understand how insider threats can be identified and stopped. The focus of the program this year is “bystander engagement.”
The phrase “If you see something, say something” is part of our lives, from airports to sporting events. These public awareness initiatives encourage individuals to report suspicious activities or behaviors to law enforcement or security personnel. The Insider Threat Awareness Month theme follows the same rules.
An engaged bystander is a coworker who can recognize activities that may put data or the organization at risk. This might include not securing devices or engaging screensavers before leaving a workstation, leaving documents or thumb drives on a vacant desktop, or emailing sensitive data to a personal account. In these instances, a friendly reminder or suggestions for safer methods of accomplishing a task can help avoid accidental data loss.
The NITTF also encourages individuals to watch for behavior that may be representative of a malicious insider or conditions that may make a coworker a threat, such as gambling problems and other addictions that could place an employee under financial duress.
The bystander engagement initiative recognizes that organizations must address malicious and non-malicious threats. When a coworker prints large volumes of sensitive data, downloads files to a USB drive, or uploads data to her personal email, she may be simply trying to work more efficiently. In this case, a colleague may be able to offer suggestions for making safer decisions.
It seems obvious that individuals should report suspicious activity, whether at a bank, airport, or business. However, there are psychological tendencies that one must overcome first. The “bystander effect” is a phenomenon that occurs when groups of people are present but do not take any action. The more people who witness a crime (for example), the less likely an individual will intervene.
According to an explanatory presentation from the Defense Visual Information Distribution Service, there can be several reasons for not acting. We will look at this from an information security standpoint.
Engaged bystanders act as a force multiplier, extending the reach of security teams and promoting a security culture. They enable organizations to scale security and embed it within each part of the business, including engineering, marketing, finance, and the executive suite.
In a sense, the information security team can be viewed as a bystander to an entire organization. Each data event (create, print, copy, share, email, etc.) has the potential to be an incident. Information security solutions like Data Loss Prevention and Insider Risk Management (learn more about insider risk) deliver visibility into these actions. While some solutions can take automated actions, there are times when an action or an alert may get to the analyst, who then must decide what action to take. A well-designed security solution gives the analysts the details they need to engage and take action, including launching the incident response plan if required. Analysts have the vision to be one of the most impactful bystanders.
|
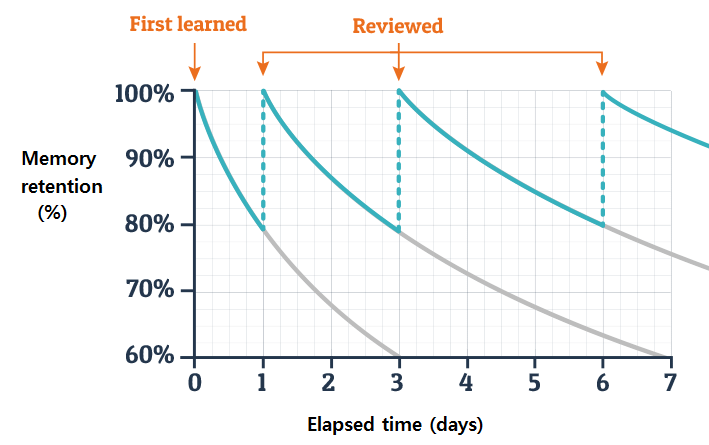
Ongoing training is a critical strategy for creating and maintaining engaged bystanders. Annual training events are not the only answer; one does not learn a new language or skill by practicing it once each year. Learning is a process that requires repetition to be effective. A study by German psychologist Hermann Ebbinghaus in the late 19th century showed that students forget over 75% of a lesson in the first week alone.
Reinforcement of lessons dramatically improves knowledge retention by keeping the information top of mind. That is why Reveal includes incident-based training. With Reveal, a policy reminder is automatically displayed when a user attempts an action that could put data at risk. It describes why the activity is flagged, policy reminders, and safe alternatives. It can even require acknowledging company policies before allowing a user to proceed. One of our customers saw immediate and significant reduction in alerts from this education.
When investigating suspicious activity, it is crucial also to protect employee privacy. Invasive employee monitoring solutions degrade trust and employee engagement and can lead to claims of bias in investigations. Analysts need to engage without their judgment being clouded, but still get the whole picture. Reveal uses data minimization and pseudonymization to hide user identities until evidence warrants unmasking. Scoped Investigations allows authorized users to request permission to unmask a user’s identity and inspect activity for a specified date range and a fixed period.
The Bystander Engagement theme emphasizes that insider threat programs are not designed to get employees in trouble. Instead, the goal is to protect people and their organizations from accidental data loss and malicious threats. By teaching people to recognize unsafe behavior, users can self-correct and help their colleagues better handle sensitive information. Augmenting this with clear policies and procedures for reporting suspicious activity will help organizations maintain a better security profile.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources
